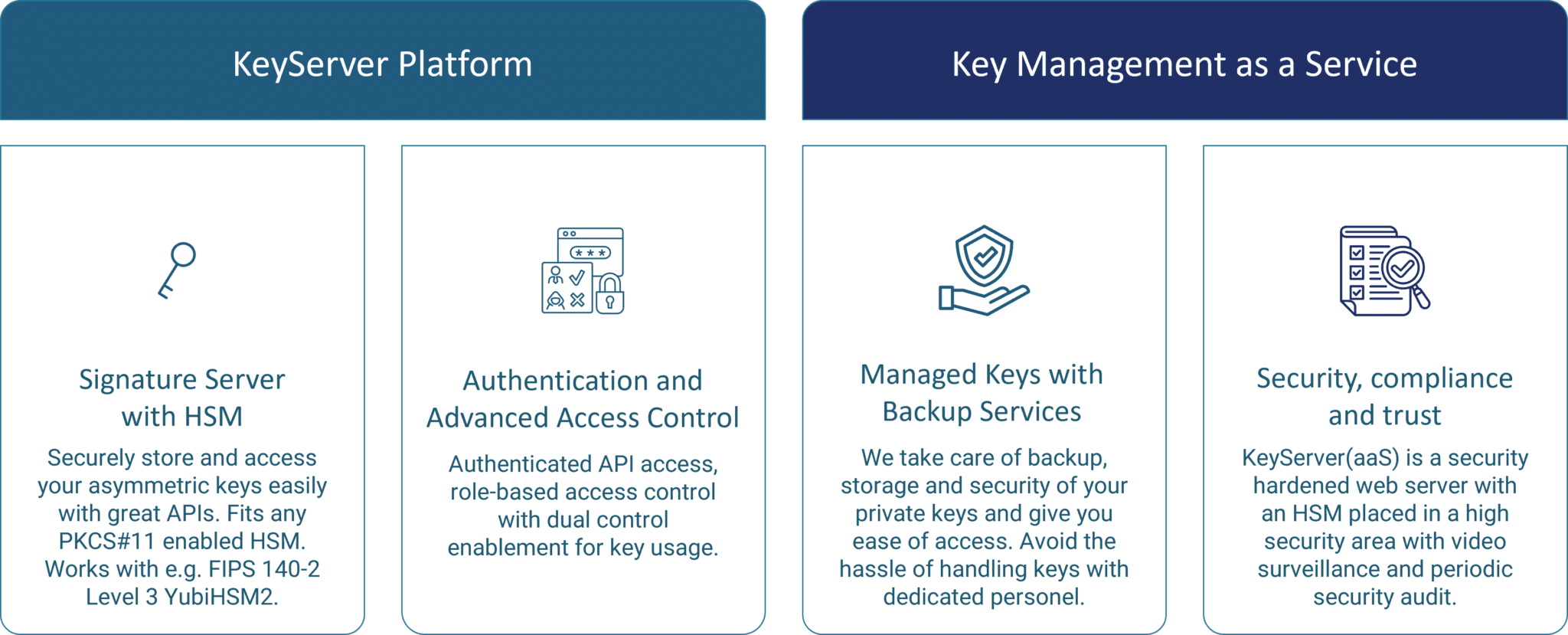
KeyServer Platform
Introduction to Key Management and Backup Solution
In today’s digital landscape, the security of sensitive data, particularly private keys, is of paramount importance. Private keys are essential for encryption, authentication, and secure communication in various applications and devices. To ensure the confidentiality, integrity, and availability of these keys, organizations need a robust Key Management and Backup Solution.
Key Management and Backup Solution is a comprehensive system designed to securely generate, store, manage, and protect private keys used in cryptographic operations. It encompasses a range of security practices and technologies aimed at safeguarding sensitive cryptographic assets against threats like theft, loss, or unauthorized access. The Cryptera KeyServer solution not only enhances security but also streamlines operational processes, reducing the risk of costly security breaches and data loss.
Advantages and benefits of a secure key management system
- Enhanced Security: A key management system employs strong encryption and access controls to safeguard private keys. It ensures that only authorized users can access and use these keys, protecting them from theft or compromise.
- Risk Mitigation: By centralizing key management and backup, organizations can mitigate the risk of data breaches and regulatory non-compliance. This reduces the likelihood of costly security incidents and associated damages.
- Data Availability: Secure key management solutions provide reliable backup and recovery mechanisms. In case of key loss or corruption, organizations can quickly restore access to encrypted data, preventing business disruption.
- Compliance and Auditing: Many industries and regulatory frameworks require organizations to demonstrate proper key management practices. A key management system facilitates compliance by maintaining audit trails and enforcing policy-based controls.
- Simplified Key Lifecycle Management: These systems automate key generation, rotation, and retirement processes, reducing the administrative burden on IT teams. This streamlines operations and ensures keys are consistently managed according to best practices.
- Secure Multi-Tenancy: Key management solutions are designed to support multiple users or entities within an organization. They enable secure partitioning of cryptographic assets to maintain data separation and access controls.
- Scalability: As an organization’s cryptographic needs to grow, a key management system can scale to accommodate additional keys and users while maintaining a high level of security.
- Interoperability: These solutions are often compatible with various cryptographic standards and protocols, making them versatile and adaptable to different use cases and environments.
- Cost-Efficiency: While implementing a robust key management system requires an initial investment, it can ultimately reduce costs associated with security incidents, downtime, and regulatory fines.
- Peace of Mind: Knowing that private keys are securely managed and backed up provides peace of mind to organizations and individuals, allowing them to focus on their core business activities without the constant worry of key-related vulnerabilities.
In conclusion, a Key Management and Backup Solution is an indispensable component of modern cybersecurity strategies. It not only fortifies the protection of private keys but also brings operational efficiencies and regulatory compliance. By investing in secure key management, organizations and individuals can safeguard their digital assets and maintain trust in an increasingly interconnected and data-driven world.
Private keys are a fundamental concept in cryptography and play a crucial role in key management systems and code signing.
Here’s a definition and explanation of private keys in these contexts:
In cryptography, a private key is a sensitive and secret piece of information used in asymmetric encryption algorithms. It is mathematically linked to a corresponding public key and is used for various cryptographic operations, including decryption, digital signatures, and authentication.
Explanation in Key Management Systems:
Key Management Systems (KMS) are used to generate, store, and manage cryptographic keys securely. Private keys are a critical component of a KMS. Here’s how private keys fit into key management systems:
- Generation: Private keys are often generated within a KMS using a cryptographically secure random number generator. They should never leave the secure environment of the KMS.
- Storage: Private keys must be stored securely to prevent unauthorized access. KMS solutions typically store private keys in hardware security modules (HSMs) or other secure storage mechanisms.
- Access Control: Access to private keys in a KMS is tightly controlled. Only authorized users or systems should have access to these keys, and strict access control policies are enforced.
Explanation in Code Signing:
Code signing is a process used to verify the authenticity and integrity of software or code by attaching a digital signature. Private keys play a vital role in code signing as follows:
- Signing: To sign code or software, a developer uses their private key to create a digital signature. This signature is unique to the developer and their private key.
- Verification: When users or systems receive signed code, they can use the corresponding public key to verify the signature. If the signature is valid, it confirms that the code has not been tampered with and originates from the legitimate developer.
In both key management systems and code signing, it is crucial to safeguard private keys.
Compromised private keys can lead to security breaches, unauthorized access, and the loss of trust in the integrity of code or cryptographic communications. Therefore, best practices include using secure hardware for key storage, implementing robust access controls, and regularly rotating keys to minimize the risk associated with private key exposure.
Introducing Cryptera's KeyServer Platform
- Robust Secure Key Storage for Code Signing
Entrust your valuable cryptographic keys to Cryptera’s KeyServer, where we provide unparalleled security and reliability. - State-of-the-Art Secure Facility
Your keys are stored and backed up in our highly secure facility, subjected to yearly security audits and rigorous compliance checks for your peace of mind. - Effortless Key Storage as a Service
Simplify key management for your connected devices with our Key Storage as a Service, streamlining your operations and enhancing security. - Fortified Security Protocols
Your private keys are protected by strong encryption, stringent access controls, and meticulous processes, ensuring the highest level of security. - Resilient Backup and Disaster Recovery
Safeguard your private keys with our robust backup and disaster recovery solutions, ensuring uninterrupted access in the face of unexpected events. - Hardware Security Modules with Uncompromising Compliance
We exclusively employ Hardware Security Modules (HSMs) that comply with FIPS 140-2 Level 2 for cryptographic security and Level 3 for physical security, guaranteeing the utmost protection. - Service Level Agreement to secure your operational performance
We offer a general SLA to our KeyServer customers to secure you get maximum level of level of support to maintain your operation. - Three Decades of Key Management Expertise
Rely on Cryptera’s 30+ years of invaluable experience in key management, leveraging our expertise to fortify your cryptographic infrastructure.