Device Onboarding
Introduction to Device Onboarding in IoT Security
In the ever-expanding landscape of the Internet of Things (IoT), device onboarding plays a critical role in ensuring the security and integrity of connected systems. Device onboarding refers to the process of adding a new IoT device to a network or ecosystem in a secure and controlled manner. This initial step sets the foundation for robust IoT security, as it establishes trust between the device and the network, while also ensuring that only authorized devices gain access.
- Enhanced Security
A secure device onboarding solution is designed to mitigate the risk of unauthorized access and cyberattacks. It uses encryption, authentication, and validation mechanisms to ensure that only legitimate devices are allowed on the network. This safeguards against potential threats and vulnerabilities. - Reduced Attack Surface
By thoroughly verifying and authenticating devices during the onboarding process, organizations can significantly reduce their attack surface. This means fewer entry points for potential hackers and a lower risk of security breaches. - Data Integrity
Secure onboarding ensures that data transmitted between devices and the central network remains confidential and tamper-proof. This is especially crucial for critical applications like healthcare, industrial control systems, and smart cities, where data integrity is paramount. - Compliance and Regulations
Many industries are subject to stringent regulations regarding data security and privacy. A secure onboarding solution helps organizations meet compliance requirements, avoiding legal consequences and reputational damage. - Efficiency
A well-designed onboarding process can streamline device provisioning, making it easier and faster to integrate new devices into the network. This efficiency can lead to cost savings and improved operational productivity. - Scalability
As IoT ecosystems grow, the ability to easily and securely onboard new devices becomes essential. A secure onboarding solution can scale to accommodate a vast number of devices without compromising security. - Remote Management
Secure device onboarding often includes remote management capabilities, allowing organizations to update firmware, change settings, and perform maintenance tasks on devices without physical access. This remote management enhances overall operational efficiency and reduces downtime. - User Confidence
End-users, whether consumers or businesses, are more likely to adopt IoT solutions when they have confidence in the security of their devices and data. A secure onboarding process can instill trust in the IoT ecosystem. - Future-Proofing
IoT devices have a long lifecycle, and security threats evolve over time. A secure onboarding solution can adapt to new security challenges, ensuring that devices remain protected throughout their operational life.
In conclusion, device onboarding is a fundamental component of IoT security. A secure onboarding solution not only safeguards against potential threats but also offers numerous advantages, including improved efficiency, compliance adherence, and scalability. As the IoT continues to grow and evolve, investing in a robust device onboarding process is essential to protect both data and the overall integrity of connected systems.
Introducing Cryptera's IoT Device Onboarding Solution
Elevate Your Device’s Security, Flexibility, and Scalability
In an increasingly interconnected world, Cryptera’s Device Onboarding stands as an indispensable all-in-one solution for provisioning and onboarding any chip to any cloud, without ever compromising on the vital aspects of security, flexibility, and scalability. As the IoT ecosystem continues to expand, our solution empowers you to maximize the compatibility of your device or IoT product with various cloud environments.
Key Benefits of Cryptera’s Device Onboarding Solution
- Zero-Touch Onboarding at Scale
Our secure device onboarding, built on the robust FIDO Device Onboard (FDO) industry standards, facilitates effortless, large-scale onboarding. Say goodbye to time-consuming setup processes and human errors. - Late Binding Capability
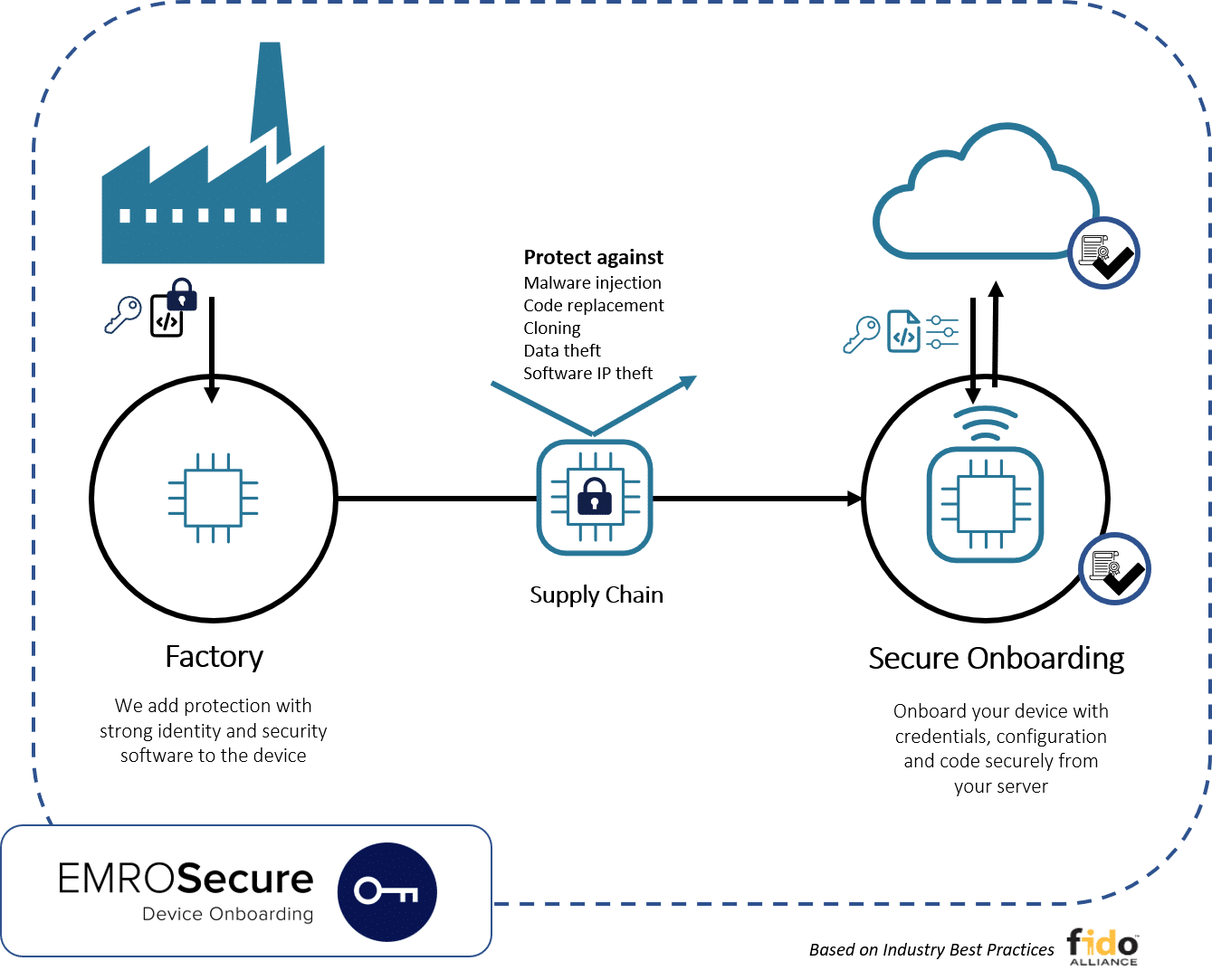
Supports late binding, allowing your product to seamlessly integrate with any cloud or server setup required throughout its lifecycle. This means you can adapt to changing backend requirements at any point in the supply chain. - Device Security Firmware
Our solution employs device security firmware to ensure that customer-specific device keys, code, and configurations are downloaded and registered securely after the device is sold. This level of configurability provides flexibility while maintaining security standards. - Simplified Supply Chain Management
By offering secure generic devices within the supply chain, EMROSecure makes manufacturing and distribution more manageable. You have the freedom to configure devices and choose backend connections according to your needs. - Trusted Identity and Security
Our solution establishes a strong device identity and a secure foundation, safeguarding your devices throughout their lifecycle. - Protection in the Supply Chain
Protects your devices during their journey through the supply chain, minimizing the risk of vulnerabilities. - Integration Versatility
It seamlessly integrates into any manufacturing facility’s process flow, ensuring smooth device onboarding. - Compatibility with Multiple Cloud Platforms
Compatibility with various cloud device management systems, offering you flexibility in choosing your cloud environment. - No Expiring Credentials
Avoid the hassle of managing expiring credentials and configurations. - Freedom from Vendor Lock-In
Our solution empowers you to avoid vendor lock-in, giving you more control over your device’s ecosystem. - Cost Efficiency
Reduce capital expenditures by streamlining device onboarding processes. - Compliance
Aligns with industry standards such as IEC 62443-4-1/4-2 and ETSI EN 303 645, ensuring regulatory compliance and peace of mind.
Download our Device Onboarding Product Sheet
Minimize the Attack Surface, Maximize Cyber Resilience
In a world where device security is paramount, Cryptera’s device security firmware and identity integration offer a proactive approach to minimizing the attack surface of your devices upon delivery. With the proposed EU Cyber Resilience Act emphasizing the importance of secure-by-default products, our solution becomes a crucial ally in achieving compliance.
By implementing our device security firmware and identity integration in the factory, you can lock down firmware and software components, reducing the risk of vulnerabilities post-production. Furthermore, our solution allows for secure-by-default configurations that can be updated until the device is powered on for the first time, ensuring your devices remain resilient and secure throughout their lifecycle.
Choose Cryptera’s EMROSecure Device Onboarding solution to elevate your IoT device’s security, flexibility, and scalability while reducing risks and ensuring regulatory compliance.

